SFP Module Coding Recognition Failures and Solutions: Module Recognition Failures, Compatibility Debugging

Network administrators routinely encounter repeated challenges with SFP modules not being recognized, resulting in loss of network connectivity and increased complexity in supporting clients. The problem arises from either an incompatibility of code or simply a recognition issue, and will lead to compromised network uptime and performance. The real issue is understanding why a particular brand of SFP module is rejected, especially if it appears compatible by established definitions related to SFP modules. Oftentimes, this issue is tied to the coding policies of particular vendor brands or the firmware verification process.
Dealing with recognition failures requires a tough and comprehensive approach to diagnose the root cause and ultimately resolve the issue. Effective compatibility debugging will pinpoint recognition errors, which ultimately create an ability to maintain consistent service delivery and reliability of the network. Now, we will share proven ways to solve “SFP module not recognized” errors, including practical troubleshooting methods and preventative strategies. Ultimately, these methods will provide a way for network teams to reduce support complexity and improve SFP deployments across a variety of hardware vendor ecosystems.
What Causes SFP Coding Errors in Modern Network Equipment?
Issues with SFP module identification and acceptance are primarily due to vendor-caused restrictive coding practices which put into place strict identification requirements. SFP modules conform to the MSA (Multi-Source Agreement), which establishes standards for physical forms and basic functions, but still allows manufacturers to build vendor codes into the EEPROM data. The codes act as “gatekeepers” for switches to understand if that specific SFP is possible to use. The EEPROM is a part of the fully compatible SFP module that communicates basic identification and configuration parameters, important for switches to identify the module. But when manufacturers produce modules with different EEPROM formatting or parsing of the values, the switch may not accept a fully functional SFP module as supported. As a step in the firmware validation process, the switches will check identifiers (EEPROMs) against the vendor’s compatibility lists; if everything doesn’t match even in the smallest way, the switch will reject the module. Gain deeper insight into how optical module coding works as a digital key for device compatibility in our comprehensive Optical Module Coding Explained article.
While coding policies established by manufacturers respect intellectual property protections and quality assurances, they become more of an obstacle than an asset to the discipline of networking. The brand of switches already stated will only accept their SFP modules and not third-party modules, even if they conform to the MSA requirements. Trying to create a balance between proprietary product ecosystems to protect the manufacturer versus the cost to set up the network efficiently between third parties creates greater conflicts for networking hardware—especially when many of these types of standards exist in the industry. The general complexity of SFP coding issues is caused by strict enforcement of codification policies, differences in EEPROM data (format or representation), and the codes as part of the switch firmware. All of these complexities account for the inevitable times when SFP modules exist that are fully capable but are rejected by the switch.
 The Data Center Catastrophe: When 200 “Compatible” SFP Modules Suddenly Went Dark
The Data Center Catastrophe: When 200 “Compatible” SFP Modules Suddenly Went Dark
During a data center upgrade, a seemingly normal firmware update resulted in a catastrophic SFP failure. SFPs that had been fully operational across a number of switches were suddenly not recognized, and over 200 SFPs experienced this large-scale failure that rendered core network services inoperable and required immediate hands-on investigation. The issue was due to a change to the vendor validation algorithm within the firmware that added stricter controls around compatibility. SFP modules that passed quality checks prior to the firmware update were now being flagged as “unsupported.” These devices were not “faulty” in the customary sense, but instead the firmware change modified the internal logic to considerably reduce the criteria acceptable to the SFP for switch connectivity.
The removed acceptance criteria revealed there existed a tenuous compatibility model among the modules attested and approved for use by the organization. Emergency mitigation measures focused on eliminating variables, confirming that only devices with the updated firmware and latest vendor validation experienced the SFP fail-to-connect condition. The failure response resulted in many emergent lessons learned and forgotten pre-deployment compatibility testing outcomes and caution in updating firmware. Even the smallest deviations to the vendor validation routines lead to massive network failures, and the work order reinforced the importance of rollback and extensive update testing prior to deployment.
How Do Firmware Updates Transform Working SFP Modules into “Unsupported Transceivers”?
Firmware upgrades often change the validation process which controls which SFP modules a switch will acknowledge, and vendors ramp up these checks, often increasing the standards of acceptance, making modules which were once verified now “unsupported” overnight. Vendors escalate these restrictions to maintain control of the ecosystem and limit modules to authorized vendors, managing to create a locking mechanism to control revenue associated with using their proprietary items. This creates another challenge during implementation where operational flexibility is lessened or, in some cases, requires replacing hardware as opposed to continuing to use workable modules. From a technical perspective, there are two types of validation enforcement, and these enforcement types are hard-coded into the firmware of the device.
One heavily restricts modules based on identifying characteristic numbers, reducing modules with any firmware contact, and the other utilizes adjustable settings to reinforce validation; some may be visible to the network admin but often locked by default. The complexity of a locked hard-coded module and adjustable configuration impacts the way a firmware update can affect module compatibility. The impact of minor software upgrades is a heightened risk with the complexity of module validation—a real-world stressor between vendor business requirements and the need for network reliability. To understand how modern high-speed transceiver standards like QSFP-DD affect legacy SFP compatibility and future-proof your network, review our detailed QSFP-DD Maximum Speed and Future Outlook guide.
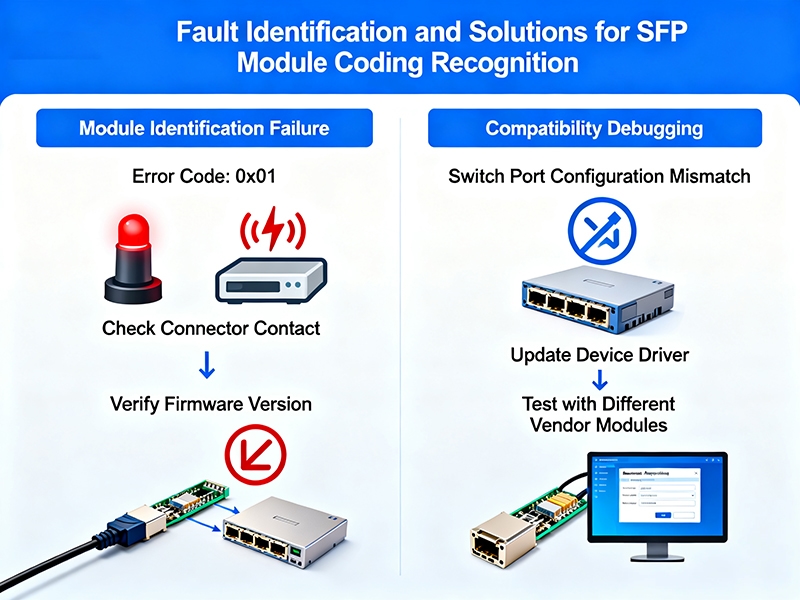
SFP Module Coding Recognition Failures and Solutions
How to Identify the Root Cause of “Module Not Recognized” Errors?
To effectively diagnose a “module not recognized” issue, a systematic, stepwise approach is advised. The first step is to simply gather status and diagnostic logs from the device through either CLI commands or SNMP queries. These tools will quickly indicate whether the SFP has been physically recognized by the system. Due to the nature of the SFP’s problem, distinguishing the root cause is paramount to defining means and methods for the potential failure, whether it be a problem with physical connections (no connections), firmware compatibility, or a bad SFP (good connections). An example of a physical connection issue is poor cable management or intermittent link stability, which may signal cabling or port problems. For help decoding vendor-specific part numbers and better identifying Cisco SFP modules, see our Cisco SFP Module Part Number Decoding resource.
The second consideration might be codes commonly associated with an SFP issue; many common error codes relate to either validation or even coding issues unique to the SFP. In either case, visual examination of the SFP or physical inspection of the fiber optic cable or ports can quickly eliminate possible failure modes associated with hardware problems or damage. Another effective troubleshooting method is module swapping. A bad SFP could have one of several issues; therefore, swapping modules is often a quick method to diagnose a possible bad SFP. Essentially, a working module would be installed into the suspected port, ideally watching to see if the error clears. If all goes well, the original SFP becomes the subject module instead.
Testing the possibly bad SFP at alternate ports or devices starts to isolate whether it is actually the SFP or the hardware port in question that has failed. Common error messages often allow the technician a means of deciphering information related to the root cause of the SFP initialization issue.
- “Transceiver not supported” generally means the module in question fails firmware-based validation.
- “GBIC invalid” typically means the module has some sort of code or classification conflict.
- “Authentication failed” usually indicates that the issue is inherent to a security check or locked vendor authorization.
For example, in one instance, a network engineer reported, in a practically academic setting, diagnosed sporadic failures from the SFP in question. System diagnostics concluded that, at some point, a failure had not been resolved, whether due to power quality, implementation, intermittent failure, etc. Although system monitoring is important and separates the issue of potential module failures, it also allows for cable management and overall documentation. Since the power was fluctuating, it caused the cycle of power not providing stable voltage to the SFP, resulting in erratic behavior. After stabilizing the electrical input to the switch, the error cleared.
This case further exemplifies the problems associated with relying solely on logs when troubleshooting any network equipment. A thorough understanding of the issues is potentially numerous when looking at failed modules. Additionally, physical and environmental logs exist, preserving proper documentation. Each of these, when thoroughly reviewed, helps in utilizing both logs and diagnostics while monitoring the environment for consistency. Utilizing both basic logic with excessive identification of environmental variables leads to root cause analysis for any degraded or failed appliances or systems. Armed with a systematic diagnostic approach, networking teams can more efficiently troubleshoot SFP-related recognition problems, a process resulting in reduced downtime and a reduction in service impacts.
 The Campus Network Recovery Mission: Restoring 500 Modules After Recognition Failure
The Campus Network Recovery Mission: Restoring 500 Modules After Recognition Failure
After completing a firmware update that disabled hundreds of SFP modules across a university campus network, time was of the essence and a structured recovery process was vital. Each vendor has specific features in place to allow managing or defaulting strict SFP validation. For example, Cisco devices provide the ability to toggle validation and compatibility enforcement using “service unsupported-transceiver,” Juniper devices have an “ignore-error” option available in transceiver diagnostic commands (to temporarily disable the strict validation mechanics), and Arista devices provide the ability to configure a relaxed authentication for a module.
Bypassing validation checks has benefits in restoring operational functionality and reducing impacts to the network, while there are risks that include voiding vendor warranties and may disqualify an organization from formal technical support. Any recovery option should be evaluated carefully for risks and considerations about bypassing SFP validation. Once an organization, through its recovery team, has established an organizational procedure for recovery from the disruption to the SFP modules, it will typically start by creating backups of configurations so that they can easily be rolled back if needed. The next step for network engineers was to apply the bypass commands one at a time and only to those switches held in the recovery team recovery plan. They were able to make these restarts and verify functionality by monitoring port statuses and logs. For instance, having rollback plans in place helped ensure a recovery from any problems immediately.
Next, validation tests began on the SFP modules. The engineers began pulling and swapping modules across ports and verifying vendor code for the SFP modules and executed other commands for details of the SFP transceivers recognized by the switch. Continual documentation of each step culminated in a simplified approach to any ongoing network maintenance. This experience solidified the necessity of knowledge of the procedure to override vendor-specific codes in SFP modules to facilitate a credible recovery plan to manage disparate warranties of the SFP modules. An organized full recovery can help an organization restore operational stability, even while managing unanticipated complexity after major firmware updates affect SFP compatibility.
 What Advanced Techniques Solve Stubborn Recognition Problems?
What Advanced Techniques Solve Stubborn Recognition Problems?
Broad compatibility testing shows a large variance in recognition rates of aftermarket SFP modules across popular switch vendors. Cisco switches recognized about 85% of the modules, while Juniper and Arista switches recognized approximately 75%.
| Vendor | Compatibility Rate | Common Failures | Workaround Success Rate |
| Cisco | 85% | Vendor code rejection | 90% |
| Juniper | 75% | Authentication failure | 80% |
| Arista | 75% | EEPROM corruption | 78% |
| HPE | 65% | Validation timeout error | 70% |
Advanced resolution steps often involve reprogramming EEPROM; this is when engineers update the module identifiers so that they match vendor specifications exactly. Low-level programming tools can allow updates to private data fields in order to get around validation barriers. But complicated steps require technical skills, and if they are applied incorrectly, they may lead to module damage. Building a process for vendor evaluation and standardizing the module procurement process, along with continuous testing for compatibility, greatly lessens the complexity of SFP use. Keeping stocks of SFPs that have already been tested and validated speeds up deployment and reduces issues related to recognition.
Preventative measures would include reliable firmware testing processes prior to any deployments, structured change management to track updates that may affect the validation algorithm, and clever inventory management that will identify modules with a higher inherent compatibility risk prior to deployment. By implementing hardware-level debugging, performing the vendor compatibility works prior, and managing prevention applies pressure against consistent recognition failures. Organizations that are masters at these processes will realize a more reliable network and fewer disruptions from SFPs. Explore detailed best practices for troubleshooting issues and repairing SFP and SFP+ transceivers in our Troubleshooting and Repairing Optical Transceiver Failures in SFP/SFP+ Modules guide.
Conclusion
In dealing with SFP coding and recognition, the successful resolution steps are procedural and include accurate diagnosis, effective troubleshooting, and forward-looking prevention. Through an understanding of error causes and applying vendor-specific practices for overrides and validation, you will recover module recognition in minimal time. Building in general management around compatibility and ongoing testing for this compatibility will create a process that produces few surprises and continues to protect your network. Successfully having the ability to navigate SFP recognition will start to gain confidence in your network team while limiting downtime caused by coding conflict and firmware changes.

 The Data Center Catastrophe: When 200 “Compatible” SFP Modules Suddenly Went Dark
The Data Center Catastrophe: When 200 “Compatible” SFP Modules Suddenly Went Dark The Campus Network Recovery Mission: Restoring 500 Modules After Recognition Failure
The Campus Network Recovery Mission: Restoring 500 Modules After Recognition Failure What Advanced Techniques Solve Stubborn Recognition Problems?
What Advanced Techniques Solve Stubborn Recognition Problems?